Examples#
Introduction#
In previous sections of this Users chapter (Access to pages, Access to Bacula resources and Access to functions) you could learn how to configure restricted access for users on three levels: pages, Bacula resources and functions. In this section you can find examples of configuring users and limited access for them using these three levels and mixing them together.
Tape operator example#
It can happen that you need to set up access in Bacularis for a person responsible for managing tape devices in the backup infrastructure. In this case, you may not want to give this person full administrative access to all Bacula resources but only restricted access to tape specific resources like: Volumes, Pools or Storage. Let’s see how to set up this access. To configure it, we will use the manual way (without wizard). This method allows you to fine-tune access details to your needs.
Step 1
Create a new role for the tape operator. Let’s call it TapeOperator.
Go to Page: Security => Tab: Roles => Button: Create new role.
In the role form, select the resources, which in this case are the pages
where the tape operator will have access. They can be:
PoolList- access to the pool list page
PoolView- access to the detailed pool view page
StorageList- access to the storage list page
StorageView- access to the single storage view page
VolumeList- access to the volume list page
VolumeView- access to the detailed volume view page
Step 2
Create a Console resource where you can define the Bacula resources
accessible to the tape operator. Go to:
Page: Security => Tab: Console ACLs => Button: Create new console.
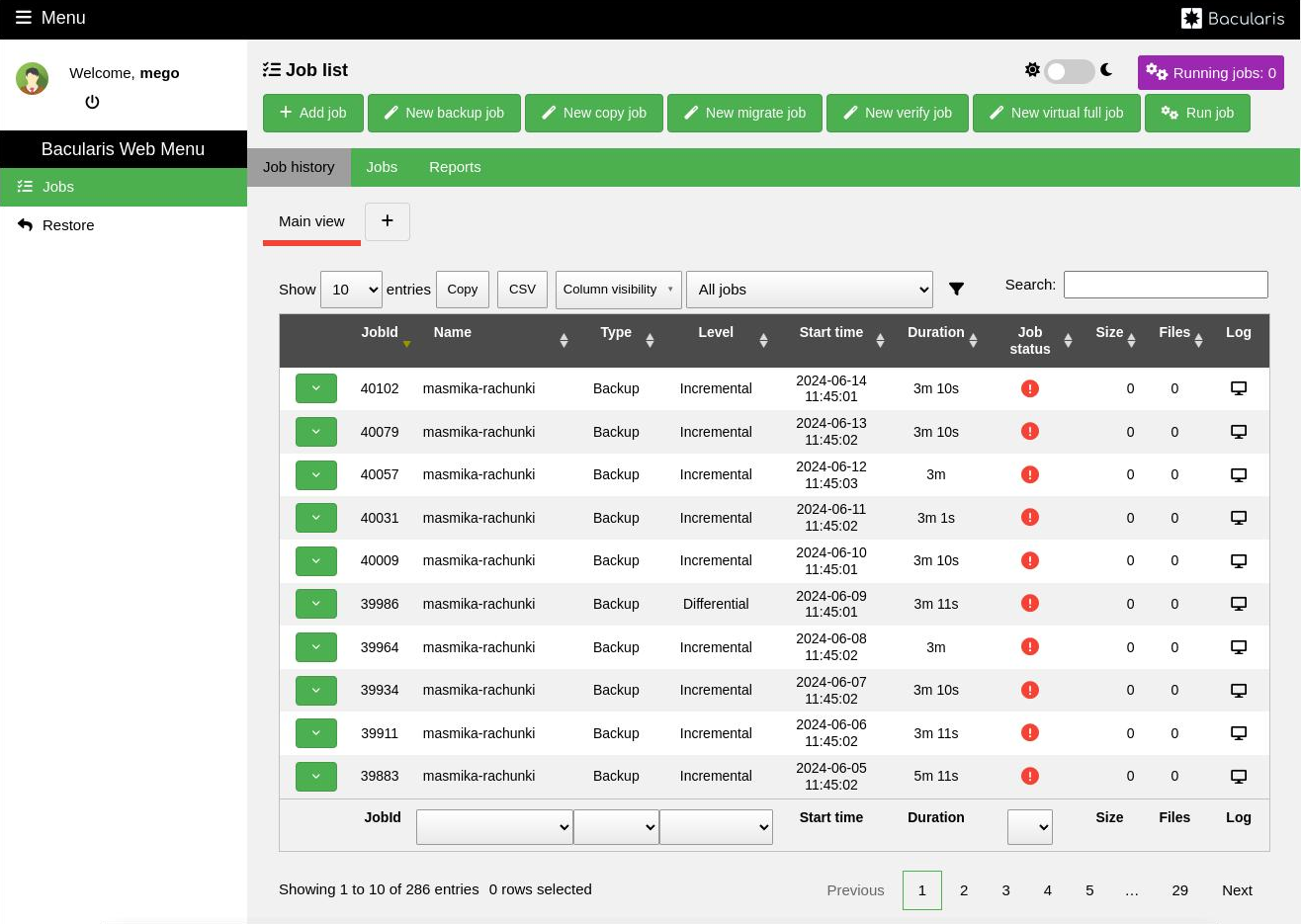
Name it TapeOperatorConsole, generate a password and select
Storage and Pool resources. In the CatalogAcl directive,
select your Catalog name or use *all*.
Minimum required CommandAcl directives:
gui- internal command
.api- internal command
.status- get storage status
.storage- list storage resources
.pool- list pool resources
delete- delete volumes
show- get basic Storage and Pool config
mount- mount volumes
umount- unmount volumes
release- release volumes
label- label volumes
update- update autochanger slots
Step 3
Create an API user account to connect with the web interface.
Use either a basic API user or an OAuth2 client if using OAuth2.
In this example, we use a basic API user. Go to:
Page: Security => Tab: API basic users => Button: Add new API basic user.
Type username and password, and check
Create dedicated Bconsole config file.
In the Console ACL field, select TapeOperatorConsole.
Save the account.
Step 4
Create a new API host connection using credentials from Step 3.
Go to Page: Security => Tab: API hosts => Button: Add new API host.
Fill in all connection parameters. For API login and
API password, use the credentials created in Step 3.
Step 5
Create a Bacularis web interface user account for the tape operator.
Go to Page: Security => Tab: Users => Button: Add new user.
Fill in the required fields. In Roles, select TapeOperator.
In API hosts, select the API host from Step 4.
Step 6
To restrict access to configuring storage daemon resources, go to:
Page: API Panel => Page: Basic users => [Select your API user] => Button: Edit.
Set Bacula resource access to read-only or no access.
Now you can log in with the tape operator account. After successful login, the web interface should appear like this:
Regular user example#
Another type of user might be someone who is not a backup administrator or operator, but just a company employee or customer. These users should only access their own backups. They should be able to log in to the web interface and restore files to their computers. Here’s how to configure them.
Step 1
Create a role named BackupAndRestore. Go to:
Page: Security => Tab: Roles => Button: Create new role.
In the Resources field, select:
JobList- job list page
JobView- job detail view
RestoreWizard- restore wizard
Alternatively, use the predefined normal role with similar access.
Step 2
Create a new API basic user (or OAuth2 if applicable).
Go to Page: Security => Tab: API basic users => Button: Add new API basic user.
Enter username and password. Create one API user per unique access setup.
Step 3
Create a new API host connection using credentials from Step 2.
Go to Page: Security => Tab: API hosts => Button: Add new API host.
Step 4
Create a Bacularis web interface user.
Go to Page: Security => Tab: Users => Button: Add new user.
In Roles, select the role from Step 1.
In API hosts, select the API host from Step 3.
Step 5
Set restricted access to jobs related to the user’s computer.
Go to Page: Security => Tab: Users => [Select user] => Button: Set access.
Select the API host and choose
Access to selected resources only.
From the job list, select only jobs relevant to the user
including at least one restore job.
In Resource permissions, optionally set all Bacula resource access to
no access or read-only.
Step 6
Adapt Console ACLs to match new access.
Go to Page: Security => Tab: Console ACLs and edit the Console ACL.
It is usually named like Console - USER_API_HOST_NAME.
To restrict job-related actions, remove these from CommandAcl:
run- re-run jobs
cancel- cancel jobs
delete- delete jobs
Now you can log in using the regular user account. You should see an interface similar to this: