Configuring Bacularis#
Installation wizard#
The installation wizard is available by default when you first start using Bacularis. It assists you with installing and configuring the application. During the setup process, you can choose whether to enable the API service and/or the web interface for this instance. One of the key questions in the wizard is whether Bacula is already installed on your system.
I have Bacula installed#
To use the Bacularis web interface with local API host, you have to configure at least the following functions in the wizard:
Step 2 - Catalog - access to the Bacula Catalog database,
Step 3 - Console - access to the Bacula console (
bconsole).
The capability to configure Bacula (with Bacula JSON tools) available in Step 4 - Config is not mandatory to start working with Bacularis, nevertheless configuration feature may be very useful in daily work with Bacula.
I don’t have Bacula installed#
If you select this option, the wizard will guide you through installing Bacula. All necessary Bacularis functions – such as the catalog and bconsole access, Bacula configuration, and Bacula component actions – will be automatically set up to work with Bacularis. Full instructions for installing Bacula using the Bacularis wizard are available in Install Bacula documentation chapter.
Bacula database access#
PostgreSQL
The supported authentication methods in pg_hba.conf configuration file are:
scram-sha-256
md5
trust
The suggested method is scram-sha-256, which is supported since PostgreSQL
version 10. If you are not able to connect Bacularis using this method,
please make sure that your password is stored in scram-sha-256 format.
You can do it for example by this SQL query:
SELECT rolpassword FROM pg_authid WHERE rolname = 'YOUR_DB_USER';
If your password is in the MD5 format, please make sure that you have set
in postgresql.conf file password_encryption directive set to
scram-sha-256.
password_encryption = 'scram-sha-256'
After changing it there is needed to set the Bacula database user password once again.
For the rest authentication methods (md5 and trust) they work with
Bacularis the same well as scram-sha-256 but they are less secure.
SUDO settings#
To complete the Bacularis wizard, you will usually need to add sudo
security policies for bconsole and the Bacula JSON tools. The wizard can
generate the appropriate sudo configuration based on the paths you enter.
You’ll find these configurations by clicking the Get sudo configuration
links during the setup steps. They look like this:
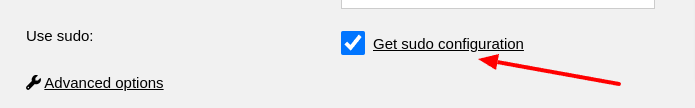
Please save the generated sudo configuration to the following file:
/etc/sudoers.d/bacularis
Below is an example of a sudoers configuration for an Apache web
server running on CentOS/RHEL:
apache ALL = (root) NOPASSWD: /usr/sbin/bconsole
apache ALL = (root) NOPASSWD: /usr/sbin/bdirjson
apache ALL = (root) NOPASSWD: /usr/sbin/bsdjson
apache ALL = (root) NOPASSWD: /usr/sbin/bfdjson
apache ALL = (root) NOPASSWD: /usr/sbin/bbconsjson
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-fd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-fd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-fd
Autochanger management#
Bacularis includes comprehensive tools for managing tape autochangers. These features allow you to:
Load tapes into drives
Unload tapes from drives
Label tapes using barcodes
Move tapes to import/export slots
Release individual or all import/export slots
Update slots using barcode data
Update slots by scanning tape volume labels
Automatic autochanger configuration#
Starting from version 4.4.0, Bacularis web interface includes a tape
storage wizard. This wizard helps you configure tape devices in the
following scenarios:
You don’t have an autochanger configured and want to add one to both Bacula and Bacularis
You already have an autochanger set up in Bacula and want to manage it via Bacularis
You want to add a standalone tape drive to Bacula
Using the tape storage wizard is the recommended method for integrating autochangers with both Bacula and Bacularis.
Video guide about adding autochanger management to Bacularis
Video guide about adding autochanger to Bacula and Bacularis
Video guide about adding single tape drive to Bacula
Manual autochanger configuration#
If you’re unable to use the tape storage wizard, you can configure the autochanger manually.
To manage an existing Bacula-configured autochanger in Bacularis:
Open the Devices page in the Bacularis API panel.
Add the autochanger and its associated tape drives.
Ensure the Autochanger name in the Storage Daemon configuration matches the name used in the Bacularis API.
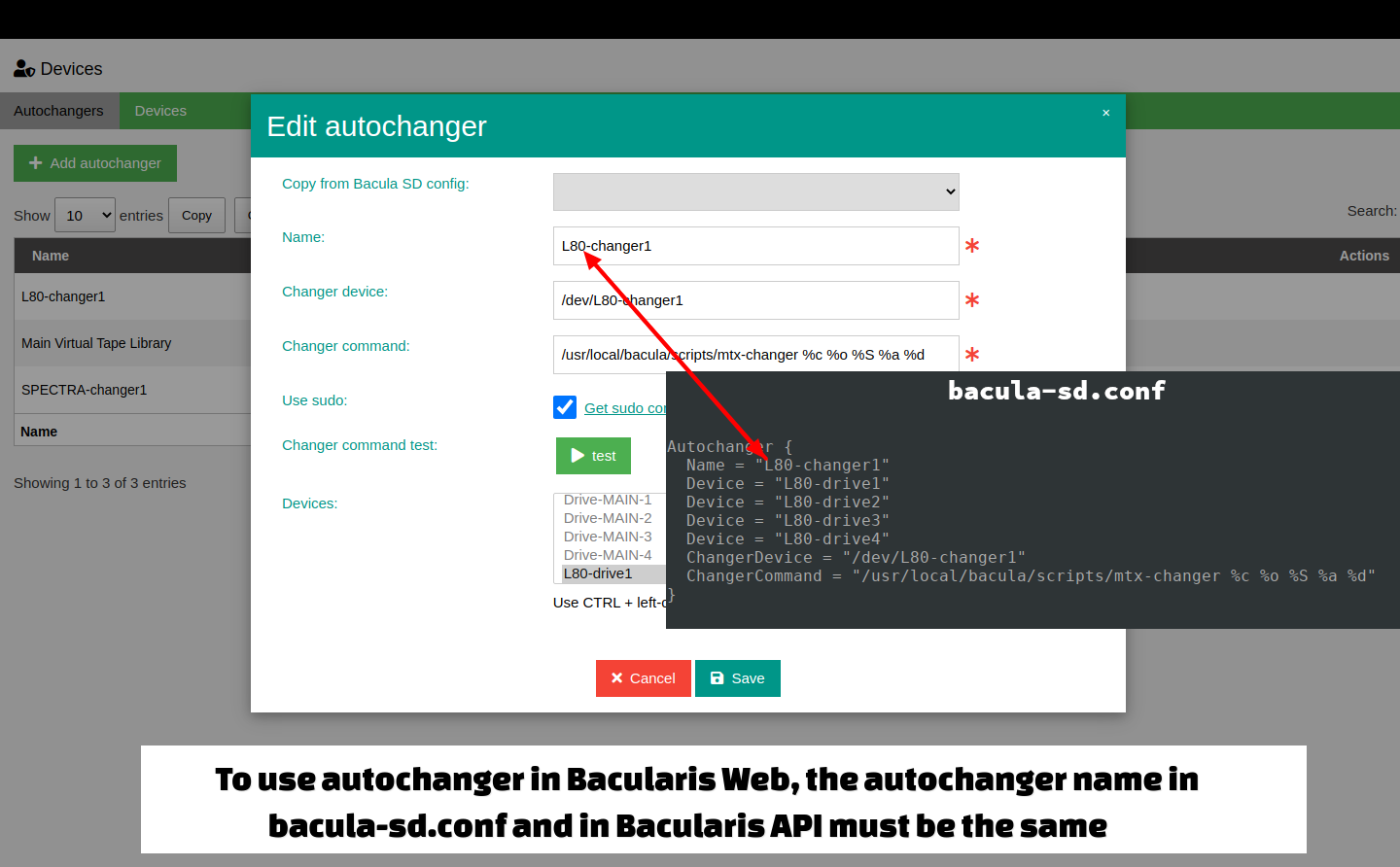
After configuring the devices in the API panel, go to the Storage page in the Bacularis web interface. Select the autochanger device and use the Manage autochanger tab to access management options for changers and drives.
Multiple API hosts#
Bacularis Web is designed to work with one or more API hosts. You can:
Connect to a single API host
Connect to multiple API hosts
Assign different API hosts to different users
This setup allows each user to manage their own API hosts through the same web interface.
In the example below, one Bacularis web interface is connected to two separate Bacularis API instances. One API can handle standard administration tasks (backups, restores, clients, etc.), while the other manages a connected tape autochanger.
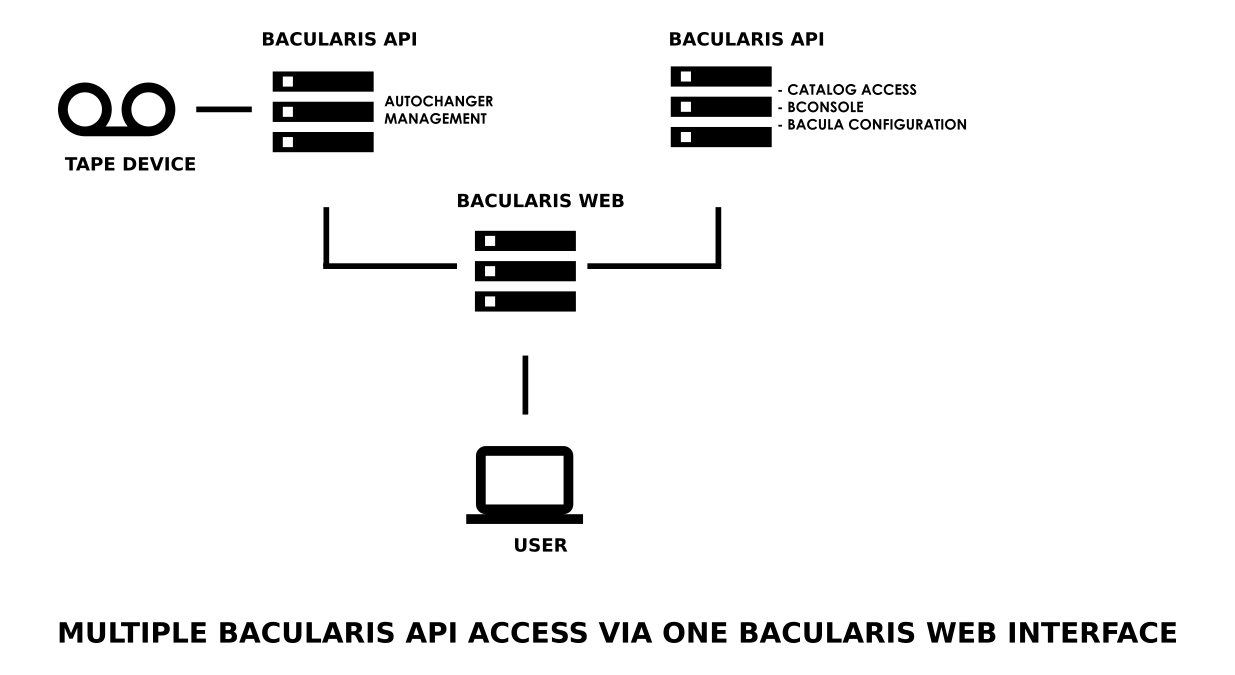
Common use cases for multiple API hosts include:
Managing Bacula Director, File Daemon, Storage Daemon, and Console on remote Bacula hosts
Operating multiple Bacula server instances
Managing autochangers (slots, tapes, import/export, labeling, updates)
Restarting remote Bacula components via Bacularis API actions (start, stop, restart)
Installing, upgrading, or removing Bacula software components
You can find more information in the Remote host management manual.
