Access to Bacula resources#
Basics#
It is possible to limit access to Bacula resources so that specific users can use only selected ones. A good example would be a company that wants employees to back up and restore only their own computers. In this case, users log in to Bacularis and see only their backups. They can perform backups and restores only for their own systems.
To restrict access to Bacula resources, Bacularis uses the Bacula Console ACL feature. You can configure this in one of the following ways:
Use the Set access button for users, API hosts, or API host groups (available since version
2.4.0).Use the New user wizard from the Security page.
Manually configure access by creating custom ACL consoles and assigning them to Basic or OAuth2 user accounts.
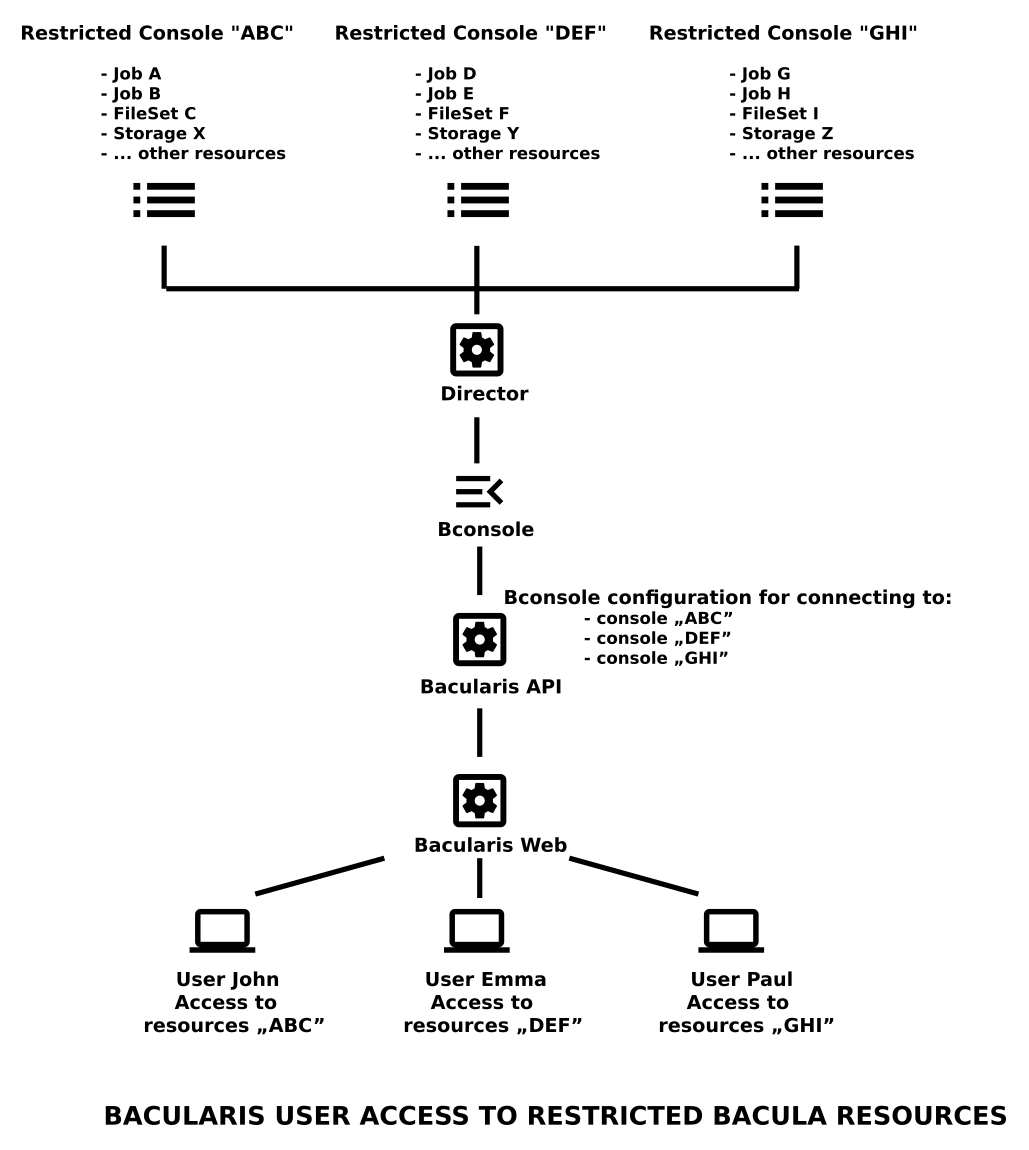
Restricted resource access can be used alongside limited page access using roles. This allows you to define which areas of Bacularis are visible and what Bacula resources users can manage.
Here is a video guide that shows how to combine page and resource access:
Configuration#
Below are the available methods to configure restricted Bacula resource access for users.
New user wizard#
Another method is using the New user wizard. This assists in creating a new user with either full or restricted access to Bacula resources.
Watch the full configuration flow in this video:
Manual Console ACL configuration#
The third method is manual configuration. Here are the steps to manually set up restricted access:
For basic API users:
Create a Console ACL with the selected Bacula resources.
Assign the console to the API basic user.
Add a new API host using the assigned basic user.
Assign this API host to the Bacularis Web user.
For OAuth2 API users:
Create a Console ACL with the selected Bacula resources.
Assign the console to the OAuth2 client account.
Add a new API host using the assigned OAuth2 account.
Assign this API host to the Bacularis Web user.
All of these steps can be done through the Bacularis Web interface— no direct changes on the API host are needed.
Resource permissions#
Since version 2.5.0, Bacularis allows setting permissions per Bacula
resource (Job, Client, FileSet, etc.). For each resource, you can define
access as read-only, read-write, or no access.
These permissions are configured per API host. This allows assigning read-only or read-write access to some resources and no access to others on a per-user basis.
This feature is especially useful when users have permission to configure Bacula through the web interface, enabling fine-grained control. You can also create read-only users who can view configuration but not modify it.
Watch this video guide to see how it works in practice:
